Mandatory Welcome Cats
/\_/\ _____________________________
____/ o o \ __ /can i have malz.. binny malz \
/~____ =ø= / \ ____________________________/
(______)__m_m)
____________________ )\._.,--....,'``.
/yes u can yes u can!\ __ /, _.. \ _\ (`._ ,.
\____________________/ `._.-(,_..'--(,_..'`-.;.'
Contents
The malwr analysis section is broken into 4 main parts, with additional reference sheets, and VM guidance.
0.1: Analysis Reference Sheet
0.2: Programming Reference Sheet
This section contains practical notes on C++ code. This could be helpful in learning to develop and break down various techniques. It is also useful to have familiarity with high level code before diving into lower level disassembly. These pages are to serve as reference sheets only. They do not cover programming concepts in much depth
C++ Basic Syntax + Windows Data Types + Win API
C++ Practical Examples
C++ Practical Examples WinAPI
1-4: Analysis Section
There are generally 4 key stages when performing malware analysis. Initial Triage, Behaviour Analysis, Static and Dynamic Analysis. The canvas sheets within this project demonstrate a variety of tooling and workflows that can be applied at each of the stages.
Below is a flow chart that shows a holistic approach on how you may reverse malicious files. It displays a high-level and generic methodology. This is not a definitive guide, and it should be adapted to meet your specific goals. For instance, if identifying IoCs is your priority, you may not be required to perform stages 3 or 4 at all. There may also be instances where you're required to switch back and fourth between different steps.
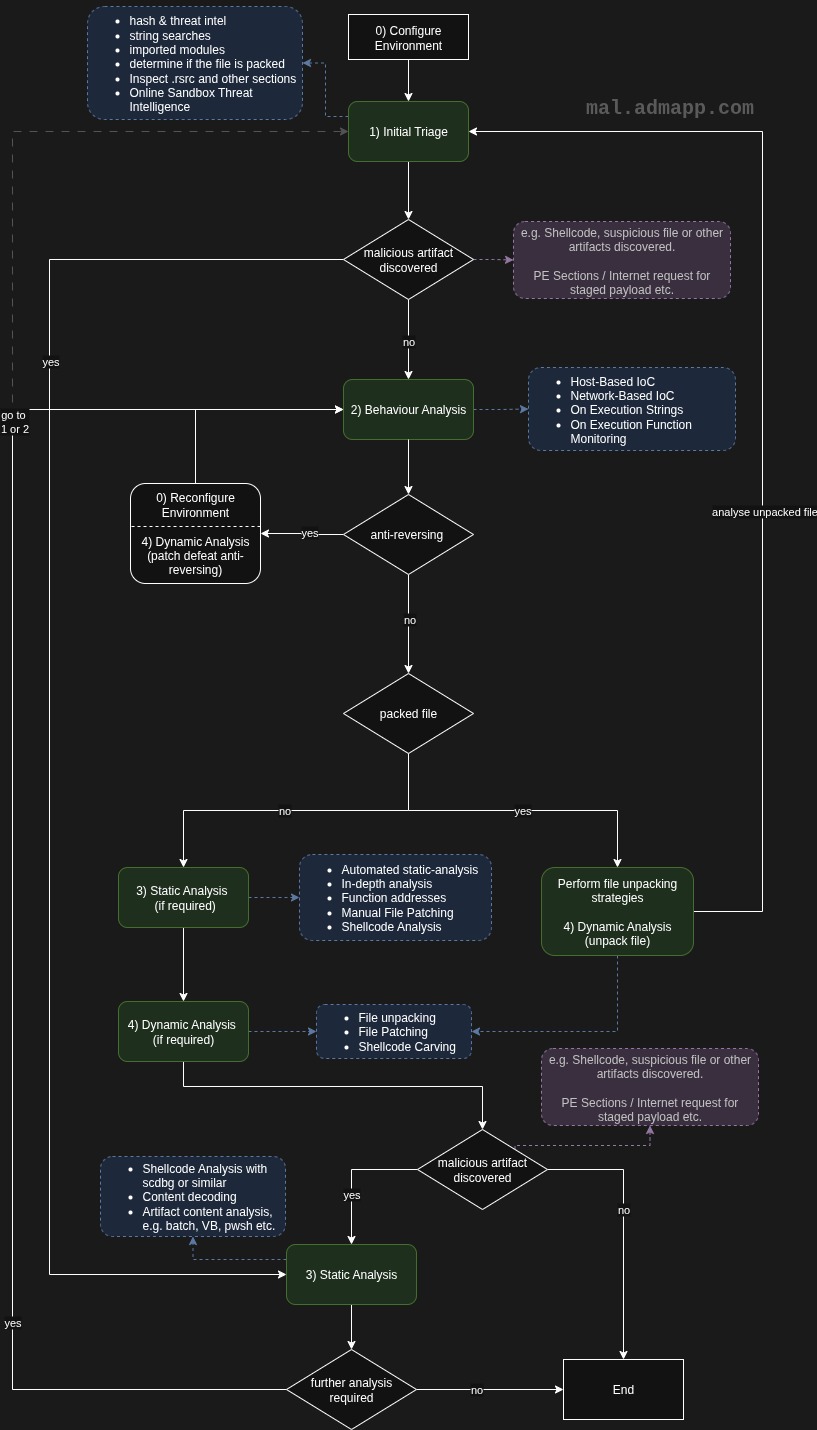
Usage Tip
- Hover over and double click on a box to automatic zoom in
- Some boxes may require you to scroll up and down in order to view all of its contents
Legend (colour-code)
Within the main (analysis) sections, there are various colours that are used for the outline of the boxes, and in some cases, the text. See the table below for a reference on what the different colours represent.
Note you may need to zoom in to see the colour of the box's outline, or you may need to click on the box for it to appear
| Colour Code | Description |
|---|---|
| Pink Box | Reference sheets found in 01-Ref Sheets section |
| Green Box | The Green Boxes represent the general workflow of the given stage (this is at the top of each analysis page) |
| Red Box | Red boxes detail the stage of analysis and the questions that the analyst should be looking to answer |
| Purple Box | Anything inside a Purple box can be executed in the Windows environment (not necessarily exclusive) |
| Yellow Box | Anything inside a Yellow box can be executed in the Linux (not necessarily exclusive) |
| Blue Box | Anything inside a Blue Box represents tips, hint, tricks and general reminders for the analyst |
| Grey Box (Green Outline) | This is the default colour, and can often be applied or run in any environment |
| Pink HIGHLIGHT | Any title with a bight pink highlight represents a powerful tool that is preferred |
Plugs
If you know anyone who might benefit from the contents of this project, I'd greatly appreciate if you could share it with them 😊
For any suggestions, updates or collaborations on this project, you can reach out to me on twitter:
👉 https://x.com/aslam4dm
Thanks for checking out this project out! If you've found this helpful, and would like to support me, or just say thanks - feel free to buy me a coffee☕ — it means a lot and helps keep the maintenance going.
@alsam4dm